
Automated Penetration Testing Service
Our automated penetration testing service will uphold your compliance and cyber insurance requirements, all whilst saving you time, costs, and resources. Introducing V-Pentest, higher frequency testing at a lower cost, which results in much greater ROI than traditional, consultative penetration tests.
Automated exploit and lateral movement assessments
No matter the shape, size or industry sector your organisation resides, our always-on security pen testing will conduct rigorous and real-time monitoring of your network and perform exploit attempts across your network to simulate a cyber attack.
After successful exploitation, our automated penetration testing service also performs post-exploitation attacks, which include privilege escalation and lateral movement within the IT environment to see if it can further infiltrate your network.
You will then receive regular reports with your network vulnerabilities so you’re always on top of points of weakness, whilst also ticking your compliance boxes and meeting cyber insurance requirements.
Benefits of our penetration testing service

Cost-effective network testing
60% less than the cost of a traditional pentest and monthly payments makes automated penetration testing a far more affordable service for organisations, providing a greater return on investment compared to a one-off assessment.

Supports compliance and cyber insurance
Backed by OSCP and OSCE-certified consultants with over 10 years of experience, our automated penetration testing services cater to and meet compliance requirements for regulated industries, including PCI, HIPAA, SOC2 and cyber insurance.
Fully scalable pen testing
V-PenTest is chargeable per IP at a small monthly cost, meaning your penetration testing can be scaled to scan an unlimited number of IPs depending on your organisation’s bespoke needs.
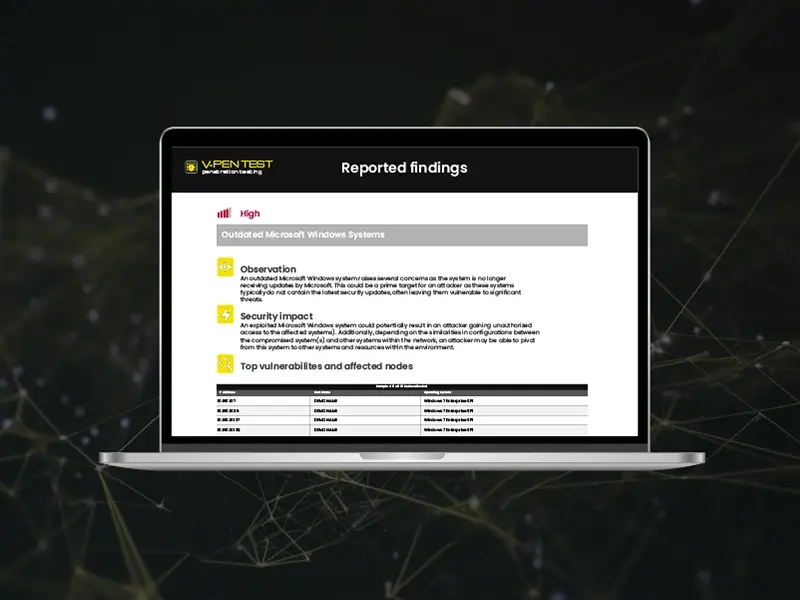
Fully automated penetration testing service
Higher frequency automated penetration testing keeps you regularly informed of the state of your cyber security to boost protection all year round and give you a better ROI.
Detailed penetration reporting
Receive detailed reports from our experts underlining your tests and points of weakness in your network, plus evidence for compliance and cyber insurance requirements.
Simple installation
Install a lightweight agent and gain the time and resources back that you would usually dedicate to a traditional, consultative penetration test.
Automated penetration testing for IT teams
Automated Penetration testing
Put your defences to the test with V-PenTest
Surpassing the expectations of a standard vulnerability scan, automated penetration testing comes with extensive catalogue of features allows for complete control over your cyber security operations.
From man-in-the-middle attacks to cracking password hashes, an escalation of privileges on your network to user impersonation, our automated penetration testing service can execute a variety of exploit attempts depending on the vulnerabilities across your network.
Detailed reporting
Prioritise points of weakness to bolster your cyber security
Our automated penetration testing service will send regular reports which outline findings from each pentest and list them by priority based on their severity and risk to your network.
Executive summaries within this report will inform your team on the severity of cyber threats in your organisation, such as compromised systems and user accounts to top vulnerabilities and affected nodes. These regular updates on your security posture go beyond traditional cyber security penetration testing, leading to a greater return on investment.
Remediate
Protect your network from future threats
Use the insights obtained from your reports to secure your network and continuously optimise your organisation for potential vulnerability threats. The V-PenTest penetration testing automation tool is the equivalent of hiring a team of 13 industry-certified experts to help you carry out a penetration test, allowing you to stay ahead of the curve when it comes to network safety.
Download our digital brochure
Fully automated security assessment
Maximise ROI with low cost network scanning
Frequent network scanning will keep your organisation informed of gaps in your network so that your organisation can stay protected into the future and are far more cost-effective than a one-off pentest.

Gain compliance with automated pen tests
The automated penetration testing service supports compliance standards such as HIPAA, SOC2, PCI and more whilst also aiding organisations with cyber security liability insurance.

High-quality penetration reports
Easy to read, understand and take advantage of, V-PenTest’s regular reports outline every vulnerability detected throughout your organisation on a regular basis.
Case Studies
Frequently asked questions
What is an automated penetration testing service?
An automated penetration testing service is a cyber security procedure in which a professional tool that simulated penetration testers (cyber security experts or ethical hackers) simulate cyber attacks on your computer systems, networks, or applications in order to pinpoint vulnerabilities that can be exploited by cybercriminals.
Once a vulnerability is identified on your network, the automated penetration testing tools exploit these vulnerabilities in a controlled manner, assessing the severity and extent of the vulnerability
The pentest will then return a full report of the vulnerabilities it finds, providing remediation advice that can be used to patch the holes in your systems and prevent unauthorised access from potential threats.
By proactively assessing and improving cyber security defences through a penetration testing service, your organisation can better protect sensitive information and minimise the impact of potential cyberattacks.
How does penetration testing work?
Penetration tests begin with careful planning, where the objectives are defined. During these preliminary talks, testers gather information using innovative automated tools to identify potential weaknesses, such as outdated software or gaps in network security.
The essential work within a penetration test comes in the exploitation phase, where ethical hackers simulate real-world cyberattacks by exploiting the identified vulnerabilities within your system. Then, testers assess the impact of successful exploits, exploring potential lateral movement within the network.
From here, the results of the penetration test are documented in a comprehensive report, covering details about discovered vulnerabilities, exploited paths, and a risk assessment of their severity. Recommendations are then provided for your team, guiding organisations in strengthening their security.
The final phase involves collaborating with the organisation to address and fix identified vulnerabilities, applying patches, configuring settings, and implementing security measures.
What is the primary goal of penetration testing?
The primary goal of a penetration test is to identify vulnerabilities and weaknesses within your systems and networks. By mimicking the actions of real attackers, penetration testers assess the security of a system and provide recommendations for improvement.
What is the role of a pen tester?
A penetration tester – or ethical hacker – tests, assesses and reinforces the cybersecurity of your system and network by simulating real-world cyberattacks. Their role involves planning and executing tests, conducting surveys and reports, and analysing vulnerabilities in your systems through automated tools and techniques.
A penetration tester will attempt to breach your security, gaining access to assess the potential impact of an actual breach. Post-exploitation, testers evaluate your system’s resilience and review the effectiveness of security controls. From this, the tester compiles detailed reports outlining vulnerabilities, exploited paths, and risk assessments, providing actionable recommendations for your organisation that strengthen your security.
By collaborating with organisations, penetration testers can catalyse the implementation of security measures, contributing to a proactive defence against evolving cyber threats.
What is ethical hacking?
An ethical hacker (also known as a white-hat hacker) is a cyber security professional who has been given authorisation to attampt to penetrate computer systems, networks, and applications to identify and address security vulnerabilities.
Unlike malicious hackers, ethical hackers use their skills and knowledge to help organisations improve their security posture and protect against cyber threats.
Ethical hackers follow strict ethical guidelines and legal boundaries while conducting penetration testing, vulnerability assessments, and other security assessments. Their goal is to proactively identify weaknesses in a system before malicious hackers can exploit them, ultimately enhancing the overall security of the organisation.
How often should organisations use penetration testing?
The ideal time between penetration testing depends on factors like industry, regulatory requirements, and changes in the IT landscape. As we move further into an “all-digital world”, the technology we harness advances rapidly. Naturally, this leaves gaps in security, be it from outdated tools or unoptimised technology.
By performing tests more frequently in response to significant system updates, new infrastructure deployments, or changes in your organisation’s processes, you stay up-to-date and ahead of the curve regarding potential new threats from hackers. We recommend monthly tests to ensure rigidness within your system and networks.
However, it’s important to note that industries with stricter compliance standards may require more frequent testing to adhere to regulatory mandates. Ultimately, organisations should uphold frequent testing and monitoring of their networks and systems so they can adapt to dynamic threat landscapes, ensuring your organisation’s security measures remain robust and effective.